What’s this all about and why exactly should I care?
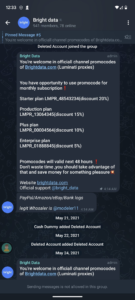
BrightData, formerly Luminati, is a proxy service offering up users’ home and cellular internet connections in trade for free software or a bit of pocket change. What lays beneath the surface is a service ripe for abuse, misuse, and carnal sins. In this blog post you will learn what people are doing with this service, how it affects you and your network, how large this problem has become, and some tips on how to prevent you from becoming a victim. Get ready for Ad Fraud, Credential Stuffing, Account Takeover, Credit Card Fraud, Scams, Malware, Phishing, Porn and possibly more that could be happening on your home or business network right now! No exaggerations, just the facts please.
Let’s dig in!
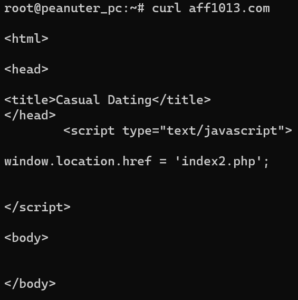
So how exactly do you convince people to let you sell their internet connection and let strangers use your network? The answer might scare you. Offer them something for nothing or give them some pocket change. Thats all it took for BrightData to grow its massive proxy network to what they claim to be 72 million residential ips, more on that figure later. For now, let’s just focus on how they get onto networks.

EarnAPP
Just like its name it’s an app for earning pocket change. Passive income is all the rage on Reddit’s r/beermoney and r/earntime . Other similar network sharing opportunities are frequently shared there. The EarnAPP platform offers multiple operating system options including Android, Windows, Mac OS, and Linux. It’s very popular among kids looking to earn a little money.
BrightSDK
BrightSDK offers application developers a way to earn money by having their user’s opt-in to BrightData’s network and run their proxy software in the background. Google’s Playstore doesn’t allow the BrightSDK to run in any mobile apps there so you will only come across this on Amazon’s Appstore, Roku’s Channelstore, in free software online, and 3rd party mobile Appstore’s. You will even find it amongst apps on your Smart TV!
HolaVPN
HolaVPN is perhaps where BrightData gets most of its residential IP addresses. By offering a free VPN service capable of bypassing streaming services geo-restricted content BrightData has a great avenue for an ever-growing userbase. Many users likely believe that the HolaVPN is just sharing their internet connection with other VPN users like themselves. They don’t realize that they are being sold to the wolfs. HolaVPN doesn’t have a good track history for being secure either. Trend Micro has even labeled it as high-risk software. It’s well known that HolaVPN users are used for ad-fraud.
HolaVPN Browser Extension
HolaVPN offers a browser extension for most common browsers. In September of 2021 Google decided to remove the HolaVPN extension from its Chrome Web Store because it contained HolaVPN Extension Malware.
BrightVPN
Every intelligence business needs to protect their branding. HolaVPN is burned and has been for years. Why not just fire up another free VPN service and name it something else!
Uncovering the secrets of the BrightData network: chatroom revelations and a glimpse into unencrypted traffic
Let me get this out of the way. I cannot confirm who is writing anything on the internet anymore then you. I leave the readers to make their own judgements and draw their own conclusions. I will share what I see and offer very little opinion on the matter.
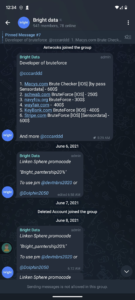
Telegram Channel “Bright Data”
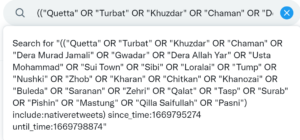
In the Telegram chatroom, “Bright data”, we find 940 members and some interesting offers. Discounts to the Brightdata proxy service, anti-fraud custom browser sales, credential stuffing software for banks and stores, and discounts on popular anti-detect / anti-fingerprint browsers using Bright in the coupon code. These things lead me to believe they may actually be the BrightData service, offering underground access to their platform, but really there is no way to tell.
Craxpro.IO Carding Forum Post
Craxpro is a self-proclaimed Cracking, Spamming, Carding, and Hacking forum who at the time of this writing has 137,656 members. Cracking, for the purposes of this forum, refers to taking large databases of compromised credentials and attempting to use them against other service providers. This is called credential stuffing normally in the news. Well in the cracking section of the forum we find this post describing various proxy providers that work well with credential stuffing software. The user also mentions Netflix CPM. I believe this is in reference to advertising fraud as CPM in the advertising world means Cost Per Million. However, it could also be a metric determining the cost per million credentials tried. Regardless, it clearly demonstrates the BrightData’s network is and has been used for credential stuffing attacks.
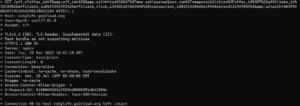
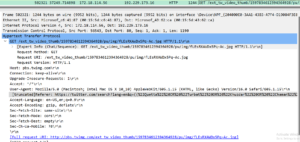
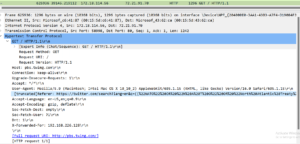
My home network’s shocking traffic from BrightData revealed
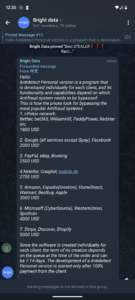
A large part of my research into residential proxy networks, DVPN’s, and other networks like them has been running the applications myself. Doing this it allows me to see what the networks are being used for. About 95% of the traffic is encrypted but that 5% can be interesting too. Networks like BrightData have just as much insight as I do, which isn’t much. We can see the IP addresses being connected to, identify domain names associated with those IP addresses, view the SSL certificates present on the IP address, see the DNS request to resolve a domain and sometimes see plaintext traffic when users neglect to use HTTPS. Without being able to see exactly what BrightData’s users are doing how can BrightData claim to be keeping the exit proxy users safe from abuse? Simple answer is they cannot. Their “Know Thy Customer” is a step in the right direction but how lucrative is it for them to look the other way on actual activity?
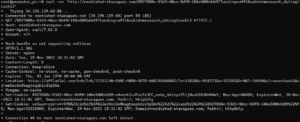
Hawaii Government
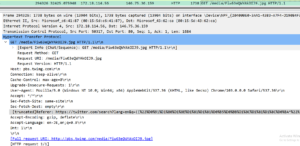
This one is particularly disturbing. This traffic happened from my network while running the HolaVPN service inside of a Windows Sandbox. The user of BrightData appears to be circumventing controls put in place by the Hawaii Government preventing people from web scraping their website. Given the starter package on BrightData costs $500 a month they were willing to spend a lot of money to obtain this information, so it was clearly valuable to them. Unsuspecting users running the HolaVPN wouldn’t have a clue they were sharing their home and cellular networks with such activity.
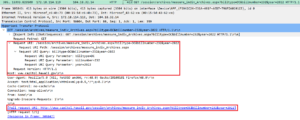
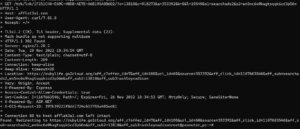
Chasing down porn redirects
Here you can see me chasing down porn redirects. The final result was an ashleymadison typo domain that goes by ashleyrndison[.]com. I reached out to ashleymadison via twitter but have got no response. I have witnessed a lot of porn going through various residential proxy networks that I have researched. Given the anonymity of these networks is so good I believe there is more going on than just porn ad fraud.
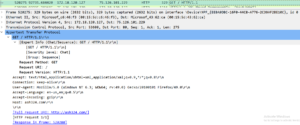
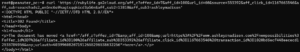
Pennsylvania’s Department of Transportation DMV Website
Here we see a request to www.dmv.penndot.gov. They appear to be logging into the website. Why would you need a $500 a month residential proxy network to log into your own dmv accounts?
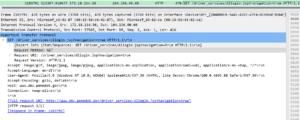
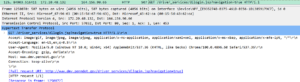
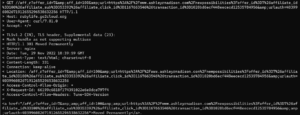
Interesting Twitter referral addresses
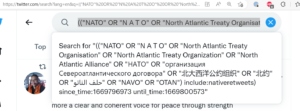
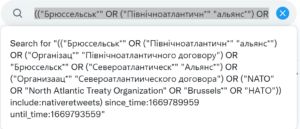
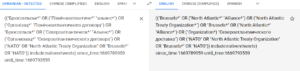
I identified some highly suspicious referral addresses in some traffic to Twitters’ twimg.com. I don’t know if it is search manipulation or intelligence collection. It is known that State sponsored threat actors use residential networks, but this doesn’t appear to be APT type activity.
Ticketmaster Scalping
I see this is how we get Taylor Swift tickets. Cool!

Malware
We do see straight up malware happening at times. Whether the customer to BrightData is infected or its the malware operator controlling their botnets is anyone’s guess.
Topics to add in the future
- Who works there and what ties do they have to the government
- How to prevent it from running on your network
- What is HolaVPN doing with upnp
- Are HolaVPN complacent in the crimes happening on there network
- How can we distinguish ad fraud from ad verification
- size of transfer potentially
- Estimated Size of the network
- What apps have been banned due to BrightData’s SDK
- How did I setup my environment to evaluate them
- What changes might I have made
- Share code that I used to extract information
- Python script to extract all dns queries from pcap
- Python script to extract web sessions from pcap
- Python script to screenshot all sites visited by my HolaVPN client
- Python script to extract hostnames from IP SSL Certificates